In a shocking revelation, blockchain intelligence firm Elliptic has provided an in-depth analysis of the infamous FTX theft, shedding light on the complex web of events surrounding the hack, subsequent money laundering, and the ongoing quest to uncover the identity of the perpetrators.
Based on blockchain analysis, the report exposes the sophisticated techniques employed to move and conceal stolen assets worth hundreds of millions of dollars.
Unraveling The FTX Hack
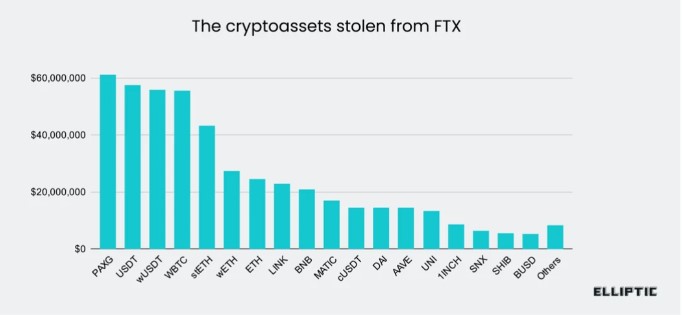
The FTX theft in November 2022 involved $477 million stolen from the Bahamas-based cryptocurrency exchange. The incident coincided with FTX’s bankruptcy filing and the subsequent arrest and charges against its CEO, Sam Bankman-Fried.
The thief’s identity behind the hack remains a mystery as the stolen assets continue to be moved and laundered on the blockchain. However, Elliptic’s investigation has provided valuable insights into the methods employed by the perpetrator.
Per the report, the thief swiftly embarked on a money laundering spree, utilizing decentralized exchanges (DEXs), cross-chain bridges, and mixers to obfuscate the trail of stolen funds.
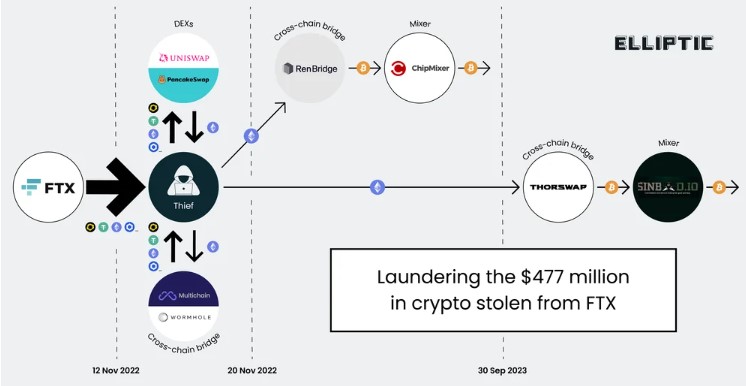
By swapping stolen tokens for native assets such as Ether (ETH) on DEXs like Uniswap and PancakeSwap, the thief evaded detection by compliance departments that typically monitor centralized exchanges.
To further complicate the tracking of funds, the stolen assets were moved across different blockchains using cross-chain bridges. The thief leveraged services like Multichain and Wormhole to transfer assets from the Binance Smart Chain and Solana blockchains to Ethereum.
Notably, the thief used RenBridge, a cross-chain bridge owned by Alameda Research, a sister company of FTX, to facilitate laundering of $74 million worth of stolen assets.
Bankruptcy May Have Enabled Internal Crypto Theft?
The stolen Ether was then converted to Bitcoin (BTC) through RenBridge, enabling the thief to access the services of mixers. Mixers, such as the notorious ChipMixer, were utilized to blend the stolen Bitcoin with funds owned by others, effectively obfuscating the origin of the assets.
However, ChipMixer was seized in an international law enforcement operation, prompting the thief to switch to Sinbad, a newly launched mixer associated with illicit activities.
While the exact identity of the thief remains unknown, Elliptic’s analysis suggests several possible scenarios.
Interestingly, the report speculates the involvement of an inside job, where individuals with access to FTX’s crypto assets may have taken advantage of the chaos surrounding the company’s bankruptcy.
Another possibility is the participation of a Russia-linked actor, given the combination of stolen assets with funds from Russia-linked criminal groups during the laundering process.
It is worth noting that the stolen assets remained dormant for several months until just before Bankman-Fried’s trial in New York.
According to the blockchain intelligence firm, this departure from the typical strategy of waiting years to move and cash out assets indicates a deliberate attempt to capitalize on the renewed attention directed towards FTX and the events of November 2022.
As of the time of writing, the token FTT of the cryptocurrency exchange FTX is trading at $1.0488, reflecting a 0.21% increase in the past 24 hours.
Featured image from Shutterstock, chart from TradingView.com









want to be on top 10 Google rankings without any upfront payment? I’m John, an SEO expert.
Email me at [email protected] with your site and keywords, and I’ll assess it.
I won’t charge until you reach the top 10. Nothing to lose! Waiting for your email.